In Brief:
-
In the world of higher education, where sensitive information is stored and constantly shared, cyberattacks are a major concern.
-
When it comes to defending against social engineering at your institution, vigilance and education are your first line of defense.
Blog Post
In the world of higher education, where sensitive information is stored and constantly shared, cyberattacks are a major concern. One common and successful type of attack is phishing, often combined with clever social engineering tactics. Since higher education institutions are becoming frequent targets, it’s important for those at your institution be informed and watchful to safeguard important information, intellectual property, and the overall security of your academic community.
Most Common Phishing Attempts
Phishing relies on human error, which is responsible for 74% of attacks. As the single most common form of cybercrime, there are an estimated 3.4 billion emails a day sent by cyber criminals designed to look like they come from trusted senders. Though they often take the form of deceptive emails and messages, they can also mimic trusted websites. These attacks can come in various guises, including:
- Email Phishing: Attackers send seemingly legitimate emails, often posing as important officials, to trick recipients into revealing sensitive information.
- Spear Phishing: A targeted form of phishing where attackers customize their messages for specific individuals, often using information gathered from social media.
- Vishing (Voice Phishing): Attackers use voice messages to trick individuals into divulging confidential information over the phone.
- SMiShing (SMS Phishing): Phishing attempts conducted through text messages, exploiting the trust users place in mobile communication.
How to Spot a Phishing Email
Whether those at your institution are tech-savvy professionals or casual internet users, knowing what to look for can make all the difference in safeguarding any sensitive information and maintaining a secure online presence. Here is a list of key traits to always be looking for when an email or message seems suspicious:
- Mismatched URLs: Always scrutinize web addresses. Phishing sites often have subtle misspellings or variations that are easy to overlook at first glance. Always double-check the domain name and ensure it precisely matches the official address, as cybercriminals often rely on these small deviations to deceive unsuspecting users.
- Unsolicited Emails: Exercise caution with unexpected emails, particularly those seeking sensitive information or immediate action, as phishers often rely on surprise. If an email comes from an unfamiliar source, take a moment to verify its legitimacy, as genuine organizations typically use established communication channels rather than resorting to emergency requests.
- Unexpected Attachments: Avoid opening attachments or clicking links in emails from unknown sources, as they may harbor malware or lead to phishing sites. Cybercriminals use seemingly harmless files or links to install malware into your system. Always exercise caution and verify the sender’s authenticity before engaging with any attachments or links.
- Requests for Personal Information: Legitimate organizations seldom request sensitive information through email or online channels. They often opt for more secure methods, such as encrypted portals or direct contact, to safeguard confidential data. Exercise caution and verify requests for sensitive information through official channels to mitigate the risk of phishing attempts.

Defending Against Social Engineering
When it comes to defending against social engineering at your institution, vigilance and education are your first lines of defense. It is crucial to conduct regular awareness programs to educate faculty, staff, and students about the dangers of these attacks. This includes recognizing phishing attempts, understanding social engineering tactics, and knowing how to report suspicious activity.
Other things you can do is implement Multi-Factor Authentication (MFA). This adds an extra layer of security by requiring users to provide multiple forms of identification. Even if credentials are compromised, an additional verification step ensures a higher level of protection. Additionally, create an Incident Response Plan. Prepare for the worst by developing a robust plan which includes steps for identifying, containing, eradicating, recovering from, and learning from security incidents. Regularly test and update the plan to ensure its effectiveness.
The Rise of Vice Society
There is a new group threatening the education sector – Vice Society. It’s a collective of Russian-based cybercriminals who are inexplicably targeting the education sector. They are notorious for their adept social engineering skills and ability to exploit the trust inherent in academic communities. By posing as trusted figures within institutions, they manipulate individuals into divulging confidential information or unwittingly aiding in cyber-attacks.
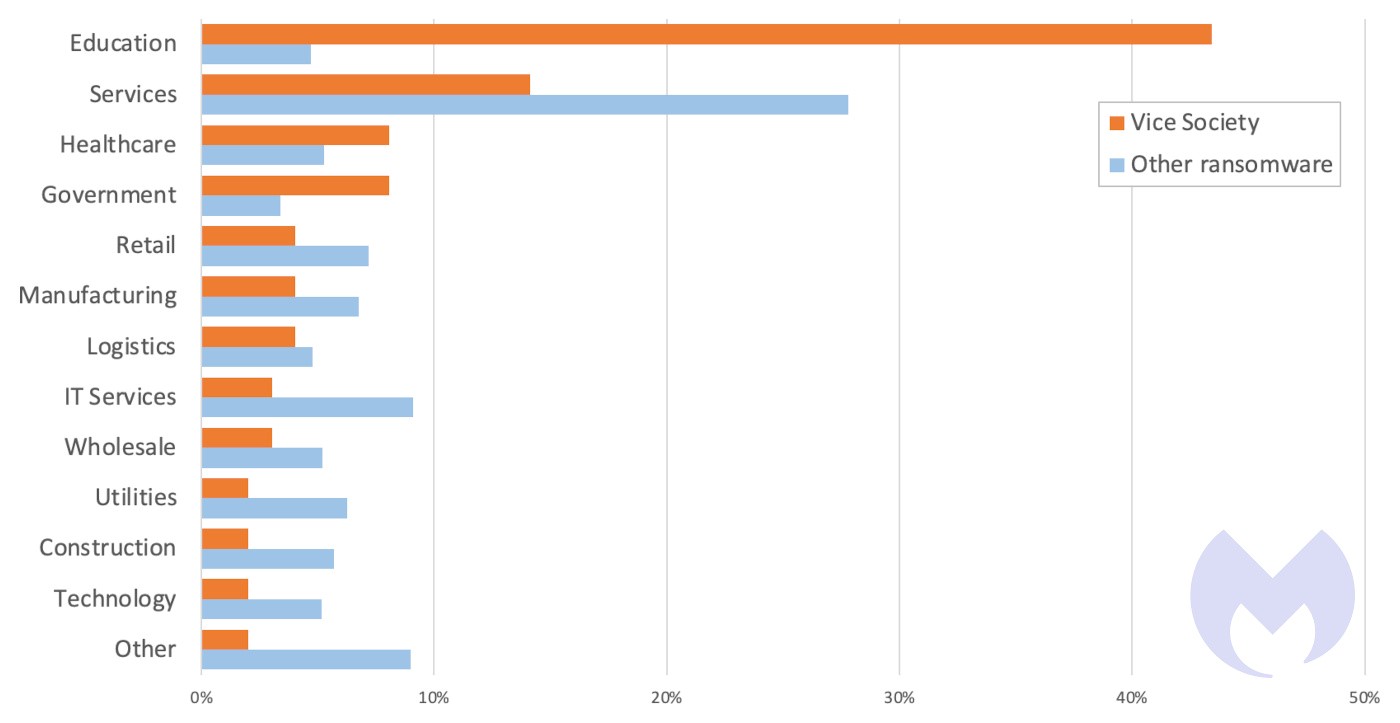
An example of how an outside group could execute an attack can be seen in the MGM Resorts data breach which occurred in September 2023. In this attack, social engineering tactics were used to gain access to employee credentials. By impersonating IT staff, they convinced employees to reveal login information, leading to a massive data breach. This incident underscores the importance of robust cybersecurity measures, heightened awareness, and continuous cybersecurity education.
Remaining Vigilant
The tactics of cybercriminals are ever-evolving, meaning higher education institutions must remain vigilant, informed, and proactive in the face of phishing and social engineering threats. By creating a culture of cybersecurity awareness, implementing robust security measures, and learning from recent incidents at other organizations, the higher education community can build a resilient defense against the ever-growing menace of cyberattacks. In doing so, you can ensure the safety and integrity of your institution and the valuable information it holds.
Want to read more on Cybersecurity?
Seven Ways to Engage in Cybersecurity Awareness Every Day
Cybersecurity Awareness Toolkit for Higher Education Institutions
Author: Nelnet Campus Commerce
